Document Type :: Assignment help (any type)
Subject :: Computer Science
Deadline :*: As Per Required
Number of Words :: As Per Required
Citation/Referencing Style :: APA
Assessment 3
For the following task you must demonstrate consistent performance in conditions that are safe and replicate the workplace. Noise levels, production flow, interruptions and time variances must be typical of those experienced in the systems administration and support field of work and include access to:
- ICT business specifications
- Information on the security environment, including relevant laws and legislation
- Existing organisational security policies, organisational expertise and knowledge
- Possible security environment, including threats to security that are, or are held to be, present in the environment
- Risk analysis tools and methodologies
- ICT security assurance specifications
- Incident scenarios
For this task you are to complete the following steps to develop, implement and evaluate an incident response plan on at least two separate occasions.
Complete the following steps to develop the incident response program on each occasion:
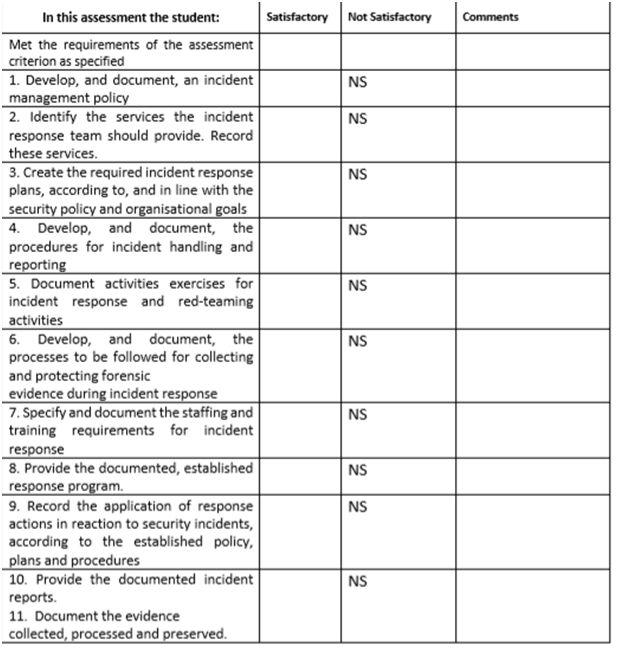
- Develop, and document, an incident management policy
- Identify the services the incident response team should provide. Record these services.
- Create the required incident response plans, according to , and in line with the security policy and organisational goals
- Develop, and document, the procedures for incident handling and reporting
- Create exercises for incident response and red-teaming activities. Document these exercises
- and activities.
- Develop, and document, the processes to be followed for collecting and protecting forensic evidence during incident response
- Specify and document the staffing and training requirements for incident response
- Establish the response program. Provide the documented, established response program. Implement the incident response program through completion of the following steps on each occasion:
- Apply response actions, in reaction to security incidents, according to the established policy, plans and procedures. Accurately record the application of response actions.
- Respond to and report incidents. Provide the documented incident reports.
- Assist in the collecting, processing and preserving of evidence. Document the evidence collected processed and preserved.
- Execute incident response plans. Provide copies of all incident response plans executed.
- Execute the planned red-teaming activities and incident response exercises. Document the red-teaming activities and incident response exercises executed.
- In a timely manner, conduct debriefing to collect the lessons learned from incidents so they can be incorporated into review plans. Document the collected lessons learned.
- Collect, analyse and report on the incident management measures. Provide the incident management measures report. On each occasion, complete the following steps to evaluate the incident response program:
- Assess the efficiency and effectiveness of incident response program activities, implementing changes as required. Provide the assessment, including changes to be implemented.
- Examine the effectiveness of the red teaming and incident response tests, training and exercises. Record this examination.
- Assess the effectiveness of communications between the incident response team and related internal and external organisations, identifying changes to be implemented, where appropriate. Document the assessment, including changes identified.
Assessment3 – Scenario ABC is a privately-owned company. Their business is to provide accounting services to small and medium sized business, such as book keeping and tax returns.
They have following staff in the head office in Sydney:
- Three Accountants
- A director
- A receptionist
- A customer support person
- And IT administrator
They have one Branch Office in Brisbane, where they have only one accountant.
In Brisbane they have 30 customers, and in Sydney they have over 150 customers.
They have following computing resources for their Staff.
- Dell Inspiron 8 GB, i5 dual core processor Laptops.
- Windows 10 Operating System
- Office 365 and One Drive for all the staff
They have a business Internet solution from Telstra. Which provides them with NBN Internet in both Head Office and Branch Office. They also have a VPN connection between Head Office and Branch Office. They have Cisco IP based telephones and VOIP solution from Telstra.
Their customer support person uses a 1300 number for incoming and outgoing customer communication.
ABC uses QuickBooks for the purpose of managing accounts for their customers. This is a cloud based software. They access it from anywhere. Some of the staff works from home sometime.
They have a server in the head office, where they have a shared folder. This folder is accessed by the staff using the VPN. The server is running on an HP ProLiant machine with Windows 2012 R2. The size of shared folder is over 10 GB. It holds all client related data.
There is a backup server, completing the backup of the shared folder every day. It is Windows Server 2016 backup software. The policy is to have a full back up every fifth Sunday. Then there is an incremental backup every day. The backup tapes are rotated to the home of the Director of company every fifth Saturday before a new full backup is taken. These are DDS3 tapes and tape drives.
Moreover, in both head office and branch office, they have a CISCO firewall and a Telstra Router. They also have a wireless access point for local area connection.
It is therefore necessary for the staff to have access to the internet, QuickBooks and the shared folder server to continue their business as usual.
Assessment 3- Two Example Scenarios
- There has been an incident where the Telstra service to the head office was not working. As IT administrator, you have the incident response program. According to the program, you have activated the incident response and operation.
The outage happened due to an issue with unplanned outage in Telstra’s exchange. The outage continued for two hours. As a contingency, you have purchased an Optus 4G wireless broadband router. You have remotely shifted your services to that router and connected your wireless access point to the Optus router, so the staff was able to continue the work. This was part of your incident response plan.
2. In another incident same day, an accountant mistakenly deleted files of a client. As part of incident response plan, you have recovered the data from the backup.